Phishing simulations that mirror real attacks
Test your team with AI-powered phishing simulations personalized through OSINT, NIST-aligned templates, and multi-channel attack scenarios covering email, deepfakes, and voice phishing.
Teams loved our cybersecurity solution
Phishing simulations that mirror real attacks
Test your team with AI-powered phishing simulations personalized through OSINT, NIST-aligned templates, and multi-channel attack scenarios covering email, deepfakes, and voice phishing.


Teams loved our cybersecurity solution
Phishing simulations that mirror real attacks
Test your team with AI-powered phishing simulations personalized through OSINT, NIST-aligned templates, and multi-channel attack scenarios covering email, deepfakes, and voice phishing.

Teams loved our cybersecurity solution
Brightside advantage
Phishing simulations that mirror real attacks
AI spear phishing simulations
AI uses OSINT to generate attacks from real employee data
Email, voice, and deepfakes
Train against email phishing, vishing, and deepfake video attack
Flexible campaign targeting
Target all employees, groups, or high-risk individuals precisely
Curated phishing templates
Curated template library organized by threat type and role
Brightside advantage
Phishing simulations that mirror real attacks
AI spear phishing simulations
AI uses OSINT to generate attacks from real employee data
Email, voice, and deepfakes
Train against email phishing, vishing, and deepfake video attack
Flexible campaign targeting
Target all employees, groups, or high-risk individuals precisely
Curated phishing templates
Curated template library organized by threat type and role
Brightside advantage
Phishing simulations that mirror real attacks
AI spear phishing simulations
AI uses OSINT to generate attacks from real employee data
Email, voice, and deepfakes
Train against email phishing, vishing, and deepfake video attack
Flexible campaign targeting
Target all employees, groups, or high-risk individuals precisely
Curated phishing templates
Curated template library organized by threat type and role
Next-gen security
Built for AI-powered phishing attacks
Our AI phishing simulations prepare your team for modern attack simulations including deepfakes, AI voice phishing, and AI-generated spear phishing using the same technologies attackers employ.

Next-gen security
Built for AI-powered phishing attacks
Our AI phishing simulations prepare your team for modern attack simulations including deepfakes, AI voice phishing, and AI-generated spear phishing using the same technologies attackers employ.

Next-gen security
Built for AI-powered phishing attacks
Our AI phishing simulations prepare your team for modern attack simulations including deepfakes, AI voice phishing, and AI-generated spear phishing using the same technologies attackers employ.

Personalized threats
Personalized spear phishing with OSINT
Our OSINT-powered AI phishing simulations analyze employee digital footprints to create personalized spear phishing attacks. AI-generated phishing mirrors real threats by using actual data hackers find about your team online.

Personalized threats
Personalized spear phishing with OSINT
Our OSINT-powered AI phishing simulations analyze employee digital footprints to create personalized spear phishing attacks. AI-generated phishing mirrors real threats by using actual data hackers find about your team online.

Personalized threats
Personalized spear phishing with OSINT
Our OSINT-powered AI phishing simulations analyze employee digital footprints to create personalized spear phishing attacks. AI-generated phishing mirrors real threats by using actual data hackers find about your team online.

Focused training
Flexible targeting for phishing simulations
Deliver phishing simulations to the right people: company-wide, select groups, or individuals. Prioritize high-risk roles and exposed employees for focused spear phishing, voice phishing, and deepfake readiness.

Focused training
Flexible targeting for phishing simulations
Deliver phishing simulations to the right people: company-wide, select groups, or individuals. Prioritize high-risk roles and exposed employees for focused spear phishing, voice phishing, and deepfake readiness.

Focused training
Flexible targeting for phishing simulations
Deliver phishing simulations to the right people: company-wide, select groups, or individuals. Prioritize high-risk roles and exposed employees for focused spear phishing, voice phishing, and deepfake readiness.

Instant templates
Curated templates for phishing simulations
A comprehensive phishing template library organized by role and threat. Choose scenarios for credential theft, ransomware, financial fraud, and more to fit each department.

Instant templates
Curated templates for phishing simulations
A comprehensive phishing template library organized by role and threat. Choose scenarios for credential theft, ransomware, financial fraud, and more to fit each department.

Instant templates
Curated templates for phishing simulations
A comprehensive phishing template library organized by role and threat. Choose scenarios for credential theft, ransomware, financial fraud, and more to fit each department.

More ways Brightside supports security teams
Privacy companion
Measure your results
Start fast
Meet Brighty
Brighty is our privacy assistant that helps employees clean up their digital footprint. When our OSINT engine finds exposed information, employees can start a chat right in their portal to fix it. Brighty walks them through each issue, explaining how we found it, why it matters, and giving easy steps to remove or hide that information.

Reporting and insights
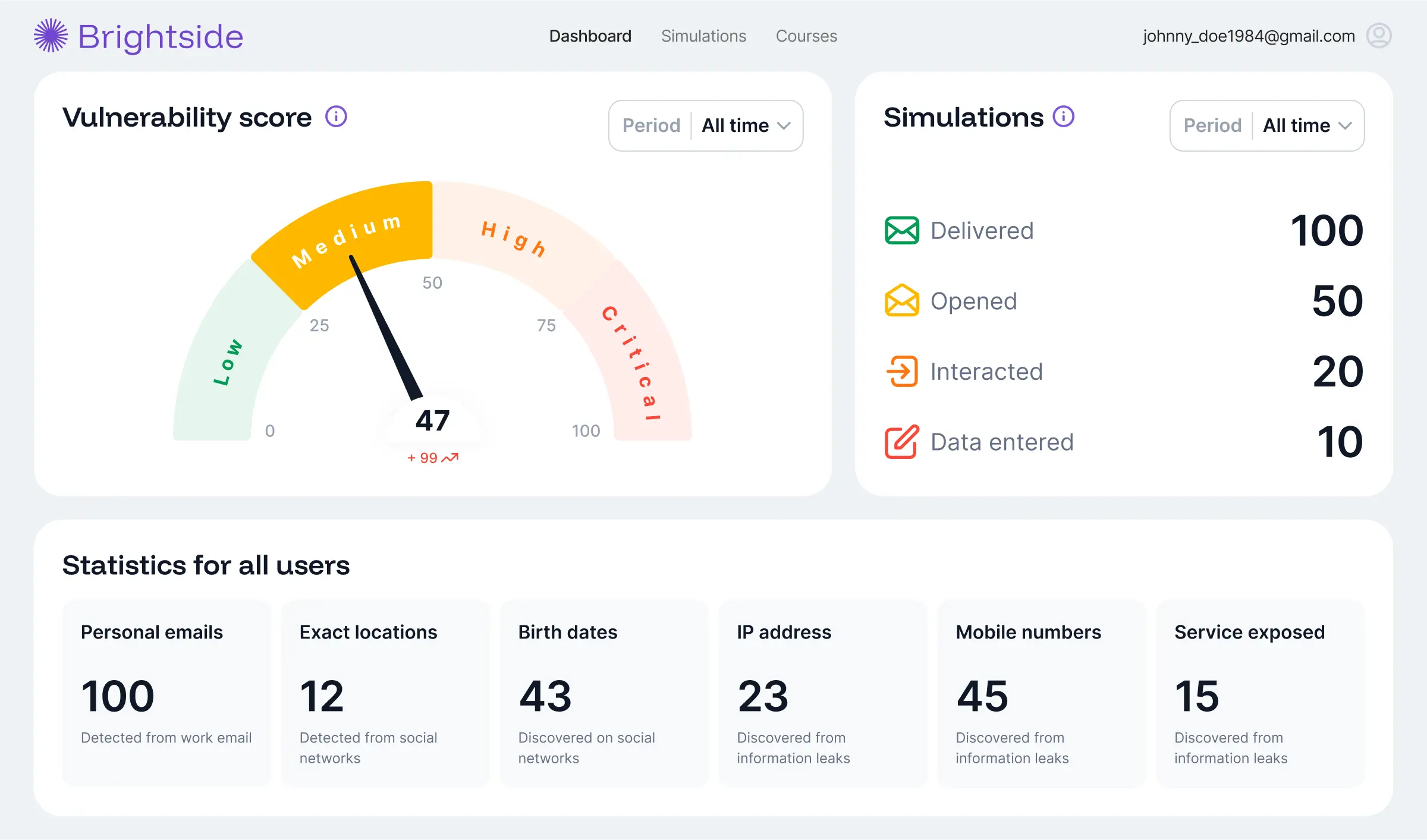
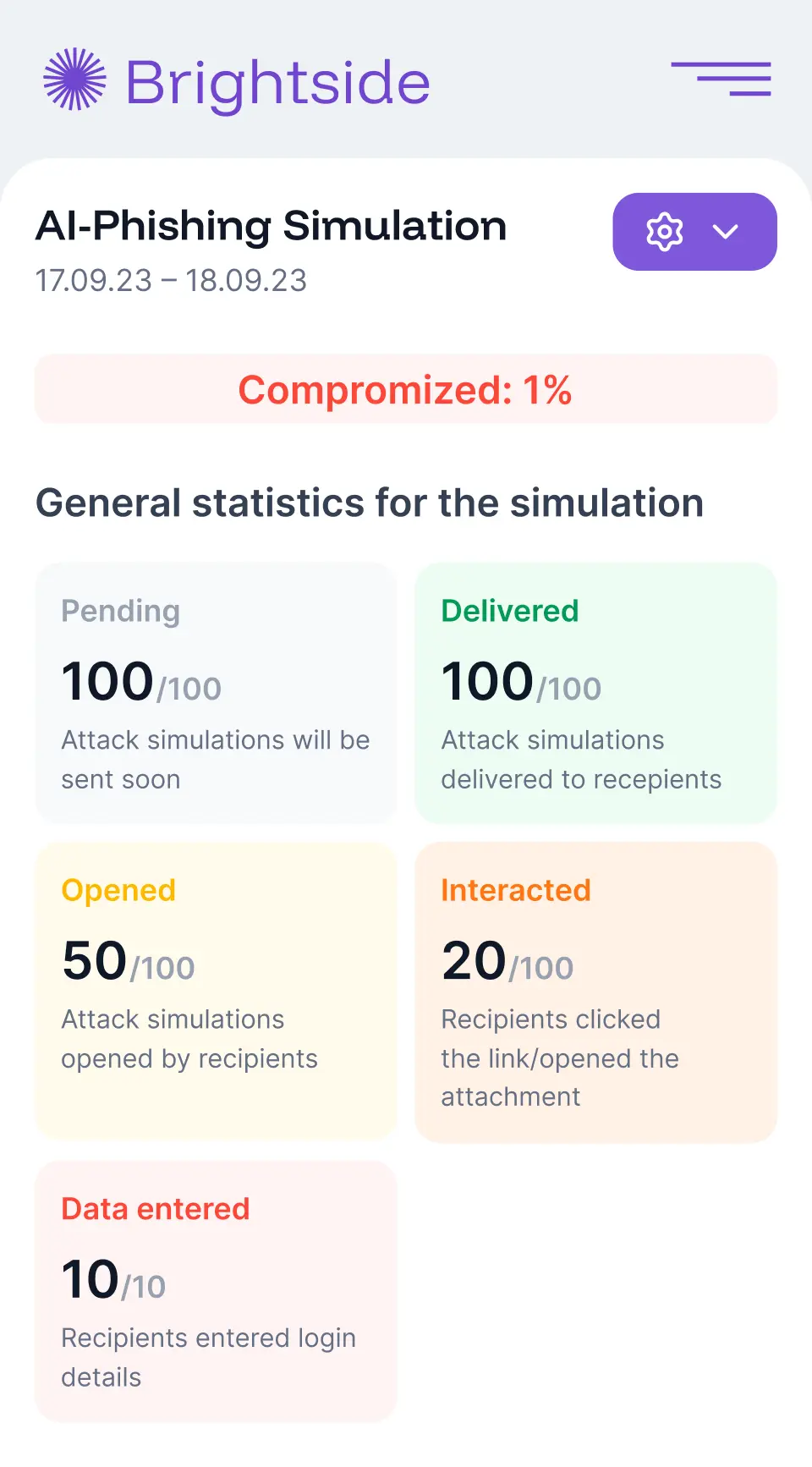
Track phishing simulation rates, course completion, vulnerability scores, and exposed data points (emails, passwords, locations) across company and individual levels. All data is aggregate; no personal details visible.

4‑step deployment
Connect with our team for a discovery call, verify your domain, whitelist our system (10 minutes with step-by-step instructions), then upload your employee list and launch personalized attack simulations.

More ways Brightside supports security teams
Privacy companion
Meet Brighty
Brighty is our privacy assistant that helps employees clean up their digital footprint. When our OSINT engine finds exposed information, employees can start a chat right in their portal to fix it. Brighty walks them through each issue, explaining how we found it, why it matters, and giving easy steps to remove or hide that information.

Reporting and insights
Track phishing simulation rates, course completion, vulnerability scores, and exposed data points (emails, passwords, locations) across company and individual levels. All data is aggregate; no personal details visible.

4‑step deployment
Connect with our team for a discovery call, verify your domain, whitelist our system (10 minutes with step-by-step instructions), then upload your employee list and launch personalized attack simulations.

More ways Brightside supports security teams
Privacy companion
Meet Brighty
Brighty is our privacy assistant that helps employees clean up their digital footprint. When our OSINT engine finds exposed information, employees can start a chat right in their portal to fix it. Brighty walks them through each issue, explaining how we found it, why it matters, and giving easy steps to remove or hide that information.

Reporting and insights
Track phishing simulation rates, course completion, vulnerability scores, and exposed data points (emails, passwords, locations) across company and individual levels. All data is aggregate; no personal details visible.

4‑step deployment
Connect with our team for a discovery call, verify your domain, whitelist our system (10 minutes with step-by-step instructions), then upload your employee list and launch personalized attack simulations.

Scalable plans
Plans for every organization size
Start free and scale with flexible pricing. Combine multiple plans and add seats as you grow—unlocking advanced AI phishing and footprint features when you need them.
Start
Free
Plan features:
Courses.
Basic
from $0.5/
m. per seat
Plan features:
Courses.
Template simulations.
Number of seats
Total (per month):
Pro
from $1.5/
m. per seat
Plan features:
Courses.
Template simulations.
AI phishing simulations.
Number of seats
Total (per month):
Ultimate
from $3.9/
m. per seat
Plan features:
Courses.
Template simulations.
AI phishing simulations.
Vishing and deepfakes.
Digital footprint for employees.
Number of seats
Total (per month):
TOTAL MONTHLY PRICE:
Need more seats? Book a call with us.
FAQ
Still have questions? Get in touch with our support.
How are you different from KnowBe4 or any other platform?
We don’t rely solely on security awareness training and template phishing simulations to protect your employees. We use automated OSINT to assess digital vulnerabilities of each team member and proactively help them remove exposed details from data brokers, unused accounts and even address dark web data leaks. This personalized approach drives employee engagement in best cybersecurity practices and reduces potential attack surface instead of just training staff to know better.
What are AI Phishing simulations?
Our genAI model uses actual employee details that are visible on the Web to automatically construct the most realistic attack simulations to each team member based on their individual exposure. Whether it is interests, locations, specific online services and more, our AI takes into account every detail to mimic how real hackers would analyze and attack each individual in the company. No need for complex setups, everything is done with the click of a button.
Are you compliant with data privacy regulations globally?
Yes, Brightside AI is fully compliant with all data privacy regulations and does not share employee personal details found online with anyone. Even company security admins only get anonymized aggregated view of data and reasons behind certain individual vulnerabilities (i.e. sensitive details are found online, personal accounts are linked to a work email, etc.).
How long does it take to start using Brightside AI with all the features?
Brightside AI does not require any integration in the internal systems to start being useful. You can upload a list of employees with their full names and work emails and digital footprint scan will begin automatically. Attack simulations can also be launched immediately after uploading the employee list. Each employee will receive onboarding communications from us, helping them get the most value out of the system. You can also immediately assign security awareness courses, which are gamified, bite-sized modules focused on real examples and practice rather than boring theory that everyone skips. To start using AI and template attack simulations, a simple whitelisting process is needed. It doesn't take more than 10 minutes and clear instructions are provided in the platform.
Can digital footprint monitoring focus just on senior leaders while all employees get security training?
Yes, Brightside AI is fully modular. You can set up full digital footprint scans for a subset of most important individuals in the company, while enrolling everyone into yearly security awareness program and automatically testing all or a group of individuals with AI-powered and template phishing simulations.
Can you explain how you scan for digital footprints on the web?
We scan all the Web (dark web and clear web) for all the traces of individual digital footprints. We run an automated OSINT engine to do the search, which reaches into dark web databases, data brokers, individual social media activity and more. This approach allows to automatically scan all team members for any and all digital vulnerabilities they might have and help them take action for better personal and corporate security.
What can you do with discovered data vulnerabilities?
If any data considered as a vulnerability was identified, Brightside AI proactively removes it from data brokers and works with individuals to remove it from unused accounts, while for the dark web we provide actionable insights on how to stay more secure since the breach has already happened.
FAQ
Still have questions? Get in touch with our support.
How are you different from KnowBe4 or any other platform?
We don’t rely solely on security awareness training and template phishing simulations to protect your employees. We use automated OSINT to assess digital vulnerabilities of each team member and proactively help them remove exposed details from data brokers, unused accounts and even address dark web data leaks. This personalized approach drives employee engagement in best cybersecurity practices and reduces potential attack surface instead of just training staff to know better.
What are AI Phishing simulations?
Our genAI model uses actual employee details that are visible on the Web to automatically construct the most realistic attack simulations to each team member based on their individual exposure. Whether it is interests, locations, specific online services and more, our AI takes into account every detail to mimic how real hackers would analyze and attack each individual in the company. No need for complex setups, everything is done with the click of a button.
Are you compliant with data privacy regulations globally?
Yes, Brightside AI is fully compliant with all data privacy regulations and does not share employee personal details found online with anyone. Even company security admins only get anonymized aggregated view of data and reasons behind certain individual vulnerabilities (i.e. sensitive details are found online, personal accounts are linked to a work email, etc.).
How long does it take to start using Brightside AI with all the features?
Brightside AI does not require any integration in the internal systems to start being useful. You can upload a list of employees with their full names and work emails and digital footprint scan will begin automatically. Attack simulations can also be launched immediately after uploading the employee list. Each employee will receive onboarding communications from us, helping them get the most value out of the system. You can also immediately assign security awareness courses, which are gamified, bite-sized modules focused on real examples and practice rather than boring theory that everyone skips. To start using AI and template attack simulations, a simple whitelisting process is needed. It doesn't take more than 10 minutes and clear instructions are provided in the platform.
Can digital footprint monitoring focus just on senior leaders while all employees get security training?
Yes, Brightside AI is fully modular. You can set up full digital footprint scans for a subset of most important individuals in the company, while enrolling everyone into yearly security awareness program and automatically testing all or a group of individuals with AI-powered and template phishing simulations.
Can you explain how you scan for digital footprints on the web?
We scan all the Web (dark web and clear web) for all the traces of individual digital footprints. We run an automated OSINT engine to do the search, which reaches into dark web databases, data brokers, individual social media activity and more. This approach allows to automatically scan all team members for any and all digital vulnerabilities they might have and help them take action for better personal and corporate security.
What can you do with discovered data vulnerabilities?
If any data considered as a vulnerability was identified, Brightside AI proactively removes it from data brokers and works with individuals to remove it from unused accounts, while for the dark web we provide actionable insights on how to stay more secure since the breach has already happened.
FAQ
Still have questions? Get in touch with our support.
How are you different from KnowBe4 or any other platform?
We don’t rely solely on security awareness training and template phishing simulations to protect your employees. We use automated OSINT to assess digital vulnerabilities of each team member and proactively help them remove exposed details from data brokers, unused accounts and even address dark web data leaks. This personalized approach drives employee engagement in best cybersecurity practices and reduces potential attack surface instead of just training staff to know better.
What are AI Phishing simulations?
Our genAI model uses actual employee details that are visible on the Web to automatically construct the most realistic attack simulations to each team member based on their individual exposure. Whether it is interests, locations, specific online services and more, our AI takes into account every detail to mimic how real hackers would analyze and attack each individual in the company. No need for complex setups, everything is done with the click of a button.
Are you compliant with data privacy regulations globally?
Yes, Brightside AI is fully compliant with all data privacy regulations and does not share employee personal details found online with anyone. Even company security admins only get anonymized aggregated view of data and reasons behind certain individual vulnerabilities (i.e. sensitive details are found online, personal accounts are linked to a work email, etc.).
How long does it take to start using Brightside AI with all the features?
Brightside AI does not require any integration in the internal systems to start being useful. You can upload a list of employees with their full names and work emails and digital footprint scan will begin automatically. Attack simulations can also be launched immediately after uploading the employee list. Each employee will receive onboarding communications from us, helping them get the most value out of the system. You can also immediately assign security awareness courses, which are gamified, bite-sized modules focused on real examples and practice rather than boring theory that everyone skips. To start using AI and template attack simulations, a simple whitelisting process is needed. It doesn't take more than 10 minutes and clear instructions are provided in the platform.
Can digital footprint monitoring focus just on senior leaders while all employees get security training?
Yes, Brightside AI is fully modular. You can set up full digital footprint scans for a subset of most important individuals in the company, while enrolling everyone into yearly security awareness program and automatically testing all or a group of individuals with AI-powered and template phishing simulations.
Can you explain how you scan for digital footprints on the web?
We scan all the Web (dark web and clear web) for all the traces of individual digital footprints. We run an automated OSINT engine to do the search, which reaches into dark web databases, data brokers, individual social media activity and more. This approach allows to automatically scan all team members for any and all digital vulnerabilities they might have and help them take action for better personal and corporate security.
What can you do with discovered data vulnerabilities?
If any data considered as a vulnerability was identified, Brightside AI proactively removes it from data brokers and works with individuals to remove it from unused accounts, while for the dark web we provide actionable insights on how to stay more secure since the breach has already happened.



